# privacy
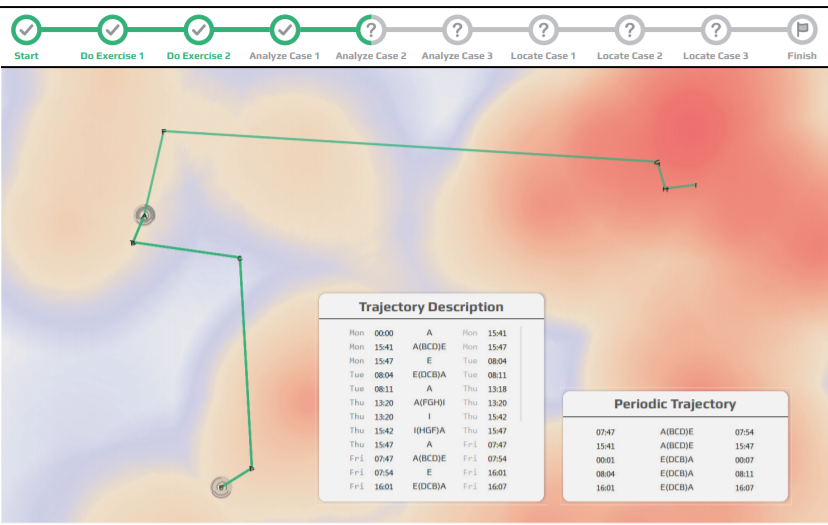
A User Study on the Capability of Three Geo-Based Features in Analyzing and Locating Trajectories
Authors: X Wang, T Gu, X Luo, X Cai, T Lao, W Chen, Y Wu, J Yu, W Chen
Visual analysis is widely applied to study human mobility due to the ability in integrating contextual information multiple data sources. Analyzing trajectory data through visualization improves the efficiency and accuracy of the analysis, yet may induce exposure of the location privacy. To balance the location privacy and analysis effectiveness, this work focuses on the behaviors of different geo-based contexts in the process of trajectory interpretation. Three types of geo-based contexts are identified after surveying 94 related literatures. We further conduct experiments to investigate their capability by evaluating how they benefit the analysis, and whether they lead to the location privacy exposure. Finally, we report and discuss interesting findings, and provide guidelines to the design of privacypreserving analysis approaches for human periodic trajectories.
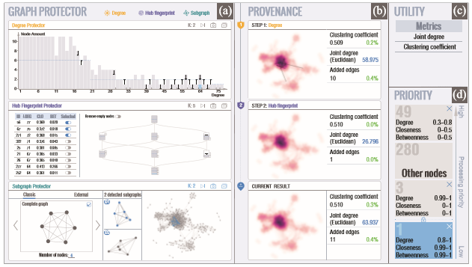
Graphprotector: a visual interface for employing and assessing multiple privacy preserving graph algorithms
Authors: X Wang, W Chen, JK Chou, C Bryan, H Guan, W Chen, R Pan, K-L Ma
Analyzing social networks reveals the relationships between individuals and groups in the data. However, such analysis can also lead to privacy exposure (whether intentionally or inadvertently): leaking the real-world identity of ostensibly anonymous individuals. Most sanitization strategies modify the graph’s structure based on hypothesized tactics that an adversary would employ. While combining multiple anonymization schemes provides a more comprehensive privacy protection, deciding the appropriate set of techniques-along with evaluating how applying the strategies will affect the utility of the anonymized results-remains a significant challenge. To address this problem, we introduce GraphProtector, a visual interface that guides a user through a privacy preservation pipeline. GraphProtector enables multiple privacy protection schemes which can be simultaneously combined together as a hybrid approach. To demonstrate the effectiveness of GraphPro tector, we report several case studies and feedback collected from interviews with expert users in various scenarios.
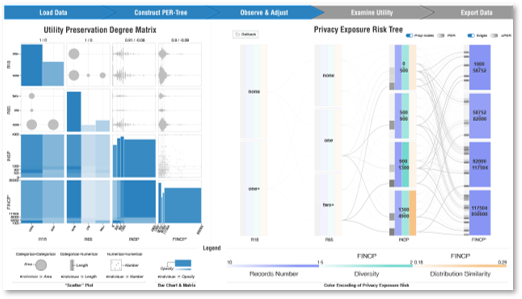
A Utility-aware Visual Approach for Anonymizing Multi-attribute Tabular Data
Authors: X Wang, JK Chou, W Chen, H Guan, W Chen, T Lao, K-L Ma
Sharing data for public usage requires sanitization to prevent sensitive information from leaking. Previous studies have presented methods for creating privacy preserving visualizations. However, few of them provide sufcient feedback to users on how much utility is reduced (or preserved) during such a process. To address this, we design a visual interface along with a data manipulation pipeline that allows users to gauge utility loss while interactively and iteratively handling privacy issues in their data. Widely known and discussed types of privacy models, i.e., syntactic anonymity and differential privacy, are integrated and compared under different use case scenarios. Case study results on a variety of examples demonstrate the effectiveness of our approach.